
Strengthening IoT Network Protocols: A Model Resilient Against Cyber Attacks
Cybersecurity Information TechnologyData Engineering受け取った 03 Jan 2024 受け入れられた 09 Feb 2024 オンラインで公開された 12 Feb 2024
Focusing on Biology, Medicine and Engineering ISSN: 2995-8067 | Quick Google Scholar
Next Full Text
Efficient Room Temperature Ethanol Vapor Sensing by Unique Fractal Features of Tin Oxide


受け取った 03 Jan 2024 受け入れられた 09 Feb 2024 オンラインで公開された 12 Feb 2024
The pervasive Internet of Things (IoT) integration has revolutionized industries such as medicine, environmental care, and urban development. The synergy between IoT devices and 5G cellular networks has further accelerated this transformation, providing ultra-high data rates and ultra-low latency. This connectivity enables various applications, including remote surgery, autonomous driving, virtual reality gaming, and AI-driven smart manufacturing. However, IoT devices’ real-time and high-volume messaging nature exposes them to potential malicious attacks. The implementation of encryption in such networks is challenging due to the constraints of IoT devices, including limited memory, storage, and processing bandwidth. In a previous work [], we proposed an ongoing key construction process, introducing a pivotal pool to enhance network security. The protocol is designed with a probability analysis to ensure the existence of a shared key between any pair of IoT devices, with the predefined probability set by the system designer. However, our earlier model faced vulnerabilities such as the “parking lot attack” and physical attacks on devices, as highlighted in the conclusion section. We present a complementary solution to address these issues, fortifying our previous protocol against cyber threats. Our approach involves the implementation of an internal Certification Authority (CA) that issues certificates for each IoT device before joining the network.
Furthermore, all encryption keys are distributed by the primary IoT device using the Unix OS ‘passwd’ mechanism. If a device “disappears,” all encryption keys are promptly replaced, ensuring continuous resilience against potential security breaches. This enhanced protocol establishes a robust security framework for IoT networks, safeguarding against internal and external threats.
The Internet of Things (IoT) encapsulates a diverse array of interconnected objects and devices utilizing sensors to gather environmental information. This information undergoes analysis, prompting devices to respond to the physical world through actuators []. The evolution of IoT technology has become imperative for modern society, facilitating seamless integration of people and things, thus forming intricate information systems through wireless sensor nodes and networks. While sharing similarities with contemporary cyber-physical systems, IoT extends its applications across various sectors, including smart energy grids, industrial control systems, healthcare, transportation, home appliances, and wearables []. Despite the operational advantages, integrating IoT technologies has introduced vulnerabilities, offering opportunities for remote adversaries. Real-world incidents and proof-of-concept attacks highlight the emergence of IoT-enabled attacks across diverse sectors []. The heightened interconnectivity of previously isolated systems creates novel attack paths for remote adversaries. Innovative communication protocols have been developed for IoT devices characterized by limited processing capacity, constrained memory, and rapid battery depletion to address these challenges. Our prior work [] introduced a protocol to address key distribution challenges within networks of small, resource-constrained devices susceptible to three distinct attacks: the parking lot attack, exposure of the keys dictionary, and physical attacks. The first vulnerability, the parking lot attack occurs when an attacker infiltrates the parking lot network, gaining access to hosts within the internal network. In our context, the proposed protocol›s initial phase involves determining the Controller device, creating a vulnerability to an «in the parking lot» attacker assuming network control, as illustrated in Figure 1.
The second vulnerability involves the exposure of the keys dictionary. If an attacker successfully intrudes on the device, they can easily access the keys’ file, necessitating protection for this critical file. The third vulnerability pertains to physical attacks on the IoT network, as depicted in Figure 2.
Therefore, this research complements the previous work and shows how the three vulnerabilities can be dealt with. The remainder of the paper is organized as follows. Section two outlines three new methods: integrating a local certificate authority method demonstrating how to configure a certificate for each device, a novel mechanism for securing the key dictionary, and a technique ensuring network security even if a device disappears. The implementation details are explained in Section 3. The upgraded and invulnerable protocol is presented in Section 4. Experiment results are detailed in Section 5. Finally, conclusions drawn from this research are presented in Section 6.
Eschenauer and Gligor [] introduced a key-management scheme incorporating selective distribution and revocation of keys to sensor nodes. This scheme relies on probabilistic key sharing within a random graph, utilizing protocols for shared-key discovery, path-key establishment, key revocation, re-keying, and incremental addition of nodes. Notably, their work does not address IoT resource constraints, a focus of our research. Alagheband and Aref [] analyzed the applicability of public key cryptography, pre-shared keys, and link-layer-oriented Key Management Systems (KMS) for sensor nodes within the IoT context. Their proposed solution employs predefined keys, while our work emphasizes the dynamic construction of keys, allowing for swift responses to unexpected events. In this context, we highlight several Key Management System (KMS) solutions tailored to the IoT domain that differ from our approach. Sciancalepore, et al. [] proposed a Key Management Protocol for mobile and industrial IoT systems, emphasizing robust key negotiations, lightweight node authentication, fast re-keying, and efficient protection against replay attacks. Their solution leverages ECC constructions, key exchange, and implicit certificates, facilitating seamless integration into security protocol exchanges like 802.15.4. Roman, et al. [] proposed key management mechanisms facilitating the negotiation of specific security credentials between two remote devices, providing shared keys for sensors within the same network. Wazid, et al. [] designed a secure, lightweight three-factor remote user authentication scheme for IoT, featuring automated validation of Internet security protocols, offline sensing node registration, and sensing node anonymity. Benslimane and BenAhmed [] introduced a lightweight key management protocol enabling constrained nodes to transmit captured data securely to an internet host. Mahmood and Ghafoor [] proposed an Efficient Key Management (EKM) scheme tailored for multiparty communication-based scenarios. Their session key management protocol employs a symmetric polynomial for group members, with the polynomial generation method incorporating security credentials and a secure hash function. While these works contribute valuable insights to IoT key management, our approach distinguishes itself by addressing resource constraints through dynamic key construction, ensuring a responsive and secure network environment. In the subsequent sections, we detail three novel methods to fortify our protocol against vulnerabilities. An overview of new IoT protocols and security threats appears in [-].
Our research contribution focuses on the development of three new methods aimed at addressing vulnerabilities within the local networks of IoT devices. Firstly, the “Local Certificate Authority” method helps prevent parking lot attacks. Secondly, the “Own Keywords Dictionary” method mitigates the risk of dictionary attacks on keys. Lastly, the “Detecting Missing Devices” method helps mitigate the risk of physical attacks on IoT devices within the local network.
Our proposed solution incorporates three novel methods to enhance the security of the IoT network: The Own/Local Certificate Authority method, the Own/Local Keywords Dictionary method, and the Detecting Missing Devices Method.
To counter the Parking Lot attack, where a malicious device poses as the Primary to seize control of key generation and distribution, we introduce the Own/Local Certificate Authority method (Figures 3,4). This method involves the following steps:
Before a device enters the network, it undergoes an “initial installation,” during which a unique encrypted code is installed. This code serves as a certificate, indicating the device’s trustworthiness to enter the home network, define itself as a Controller or node, and communicate with other devices in the network [].
An identification step is initiated for each device before it connects to the network. Only after identification can the primary be determined (if one does not exist in the network) or identified as a device in the home network.
A daemon, a background process, is created to check the device’s reliability. Once connected to the network, the daemon verifies the certificate file’s existence, correctness, and reliability. Consider that the certificate file may not exist, is not valid, and/or is invalid (fake).
During the initialization of the Controller, a “Key Pool” is created, encrypted, and saved in the device’s memory. This “Key Pool” is the heart of our method, because the proposed protocol relies on probabilistic key sharing among the IoT devices of a random graph that ensures the existence of a common key between any pair of IoT devices in a predefined probability which is set by the system designer.
The Controller generates a public key for the home network. When a new device joins the home network, it receives, from the Controller, the shared public key and a group of keys with randomly selected indexes from the key pool. They ensure the home network’s public key is shared in a conversation between two devices.
It checks to ensure that both devices are from the same home network and that the public shared key for the home network is equal. They find a shared key to encrypt messages and securely exchange information.
When a device wants to communicate with another, it sends an encrypted message using AES encryption. The encryption key is the shared key. The receiving device decrypts the message using the same key.
We introduce the Own Keywords Dictionary method to mitigate the risk of dictionary key attacks on an IoT device within the local network. This could lead to key discovery and compromise the network. This mechanism operates like the safeguarding mechanism for password and shadow files in the UNIX system. Access to the keyword file is restricted, mirroring the root’s protection of critical system files (e.g., cat/keyword: Permission denied). The keyword file comprises the following data:
An example of the records in the keyword file (Figure 5).
To prevent a malicious opponent from “snatching” a device and extracting the information required to hack the network, a dedicated daemon in the Controller device checks all active devices. The test will be performed as follows:
1) For each time frame (e.g., 20 minutes), the Controller sends a ping to each IoT device and maintains a list of all those who returned an answer (Reply from) and those who did not (Request timed out).
2) Select those who did not return an answer from the list, wait a time (e.g., 3 minutes), and send a ping again.
3) After three unanswered attempts, the Controller exchanges keys for all IoT devices in the local network (Repeat steps 3 through 6).
An example of the dedicated daemon (just in the Controller) that starts running immediately after distributing the keys to all devices:
1) Every 20 minutes, ping to all devices in the local network
>> ping device-1
Pinging device-1 with 32 bytes of data:
Reply from device-1: bytes=32 time=222ms TTL=115
…
Ping statistics for device-1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
…
>> ping device-2
Pinging device-2 with 32 bytes of data:
Request timed out.
…
Ping statistics for device-2:
…
…
>>ping device-n
…
2) Since there is no response from device 2, after 3 minutes
>> ping device-2
Pinging device-2 with 32 bytes of data:
Request timed out.
…
Ping statistics for device-2:
…
3) Since there is no response from device 2, after 3 minutes
>> ping device-2
Pinging device-2 with 32 bytes of data:
Request timed out.
…
Ping statistics for device-2:
…
4) Immediately after the third failure, the Controller sends new keys to all devices and sends a cancellation message on the previous keys.
Own keywords dictionary method:
Pseudo code for the key security mechanism
For every device:
Loop:
Compare the encryption result (of each index) to all results in the “Index of Key” column
o If a match was found:
Move to the “Keys” column in the same row, decrypt the encryption result, and return it
o Otherwise:
Return “match was not found.”
end loop;
The root also protects this.
Detecting missing devices method: The following Python code implements the “Detecting Missing Devices” Method
(Figure 6).
The new immune protocol
Following, we describe the protocol in further detail:
1) Preliminary step
2) Determining the controller device as soon as an IoT device enters the network, it broadcasts two messages on the network: “IS THERE Controller & myCertificate” and waits for some time for a response:
3) The Controller defines the key pool size
4) The Controller requests the manufacturing of distributed keys
5) Creation of distributed keys by each node in the network
6) Distribution of keys
7) Finding a shared key
8) Secure network
9) Missing devices detected
In this section, we demonstrate the operation of the innovative protocol (appears in section 3) we developed in this research with the new approaches to dealing with the vulnerabilities of the previous protocol. We performed experiments in our laboratory with 3 Raspberry Pi 3 Model devices (#1: 10.0.0.26, #2: 10.0.0.10, #3: 10.0.0.5).
Step 1: Preliminary step as described in section 4, step 1.
Updating a local certificate for each IoT device by the network manager, as follows (Figure 7).
Step 2: Determine who the Controller device is as described in section 4, step 2.
This operation is done by device #1, which looks for the Controller device on the network, sends a message in broadcast with its certificate to other devices, and declares itself a Controller. The other instruments would ignore this message if the device were without a certificate (Figure 8).
Step 3: The Controller defines the key-pool size as described in section 4, step 3.
Now, Device #1 calculates the required pool of keys and the number of keys each device will receive, ensuring an overlap of at least one key between any two devices on this network with a 90% probability. In our case (3 devices), a pool of 152 and 16 keys per device is required (Figure 9).
Step 4: Controller requests manufacturing of distributed keys as described in section 4, step 4.
Device #1 (the Controller) sends a message in broadcast for all devices to generate keys (Figure 10).
Step 5: Create distributed keys by each node in the network as described in section 4, step 5.
Each node in the network generates keys as required. These keys are sent to the Controller encrypted with the Controller’s public key (Figure 11).
Step 6: Distribution of keys as described in section 4,
step 6.
Each device generates a private and public RSA key and sends the public key to the Controller with his certificate. The Controller (#1) can now encrypt the subset of keys and send it to the other devices (#2 and #3) (Figure 12).
Step 7: Finding a shared key as described in section 4, step 7
Each node that receives keys sends an “I AM ON THE NETWORK & myCertificate” message in the broadcast. When another node wants to exchange encrypted messages, it sends CLIENT START SESSION & myCertificate messages with its list of indexes (of keys). Here, device #2 got a message from device #1 to find a shared key (148) (Figure 13).
Step 8: Secure network as described in section 4, step 8
Here, node #2 wants to communicate with node #3 (none of them is the Controller), and the shared key between them is 42. node #2 sends a MESSAGE ENC DATA message in which AES encrypts the information it wants to transmit, and the encryption key is the shared key. Node #3 decrypts with the same key (Figure 14).
Step 9: Detection of missing devices as described in section 4, step 8
To ensure that all devices in the network are alive, the Controller (#1) sends a ping message every 20 minutes to each node (e.g., #3). If there is no answer from a particular device, the current batch of keys is canceled and immediately replaced (Figure 15).
In conclusion, our endeavors to enhance the security of IoT networks have led to significant strides, building upon the foundation laid in our previous work as mentioned previously. The initial protocol addressed key construction and distribution challenges for IoT devices with limited resources. As a complementary extension, this paper introduces a fortified protocol designed to withstand potential cyberattacks.
1) Device-specific certificates: We implemented unique certificates for each IoT device, enhancing trust and preventing unauthorized access to the network during the initial installation phase.
2) Robust key dictionary security: Recognizing the vulnerability of the key dictionary, we implemented stringent security measures, restricting unauthorized access and fortifying the encryption keys against potential breaches.
3) Swift key replacement mechanism: In response to the disappearance of an IoT device, we introduced a mechanism for immediate key replacement. This proactive measure ensures continuous network security, mitigating the risk of compromised keys.
While the enhancements show promise in controlled laboratory conditions with three devices, future work involves expanding the scope of testing to a larger scale. Real-world deployment and evaluation will be pivotal in understanding the practicality and effectiveness of the enhanced protocol in diverse IoT environments. The following aspects will be explored in future work:
1) Large-scale testing: Rigorous testing on a larger scale will provide insights into the protocol’s performance and resilience under dynamic and extensive IoT deployments.
2) Real-world deployment: Practical implementation of the enhanced protocol in real-world scenarios will be crucial in validating its effectiveness and identifying any unforeseen challenges.
3) Dynamic IoT environments: Future work will consider the adaptability of the protocol to various IoT environments, ensuring its effectiveness in diverse and dynamic settings.
4) Security audits: Continuous security audits and assessments will be conducted to identify and address any emerging threats or vulnerabilities in the evolving landscape of IoT security.
In summary, our enhanced protocol represents a crucial step towards creating a robust and secure IoT ecosystem. Future endeavors will focus on translating these advancements into practical solutions, addressing the ever-evolving challenges in IoT security.
Leshem G, David E, Domb M. Probability-Based Keys Sharing for IoT Security. ICSEE International Conference on the Science of Electrical Engineering. 2018.
Gubbi J, Buyya R, Marusic S, Palaniswami M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013; 29:1645–1660.
Sundmaeker H, Guillemin P, Friess P, Woelfflé S. Vision and challenges for realizing the Internet of Things. In Cluster of European Research Projects on the Internet of Things; European Commission: Brussels, 2010; 3: 34–36.
Stellios I, Kotzanikolaou P, Psarakis M, Alcaraz C, Lopez J. A survey of IoT-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Commun. Surv. Tutor. 2018; 20:3453–3495.
Eschenauer L, Gligor VD. A key-management scheme for distributed sensor networks. Proceedings of the 9th ACM conference on Computer and communications security, Washington DC.11-2002; 341-47.
Alagheband MR, Aref MR. Dynamic and secure key management model for hierarchical heterogeneous sensor networks. Iet Information Security [IF: 1.04]. DOI — 10.1049/iet-ifs.2012.0144, 2012
Sciancalepore S, Piro G, Boggia G, Bianchi G. Key Management Protocol with Implicit Certificates for IoT systems. Proceedings of the 2015 Workshop on IoT challenges in Mobile and Industrial Systems. Florence, Italy. ACM, NY, USA. 2015; 37-42. ISBN: 978-1-4503-3502-7
Roman R, Alcaraz C, Lopez J. Key management systems for sensor networks in the context of the Internet of Things. Nicolas Sklavos, Computers & Electrical Engineering. 2011; 37:2; Pages 147-159.
Wazid M, Das AK, Odelu V. Design of Secure User Authenticated Key Management Protocol for Generic IoT Networks. IEEE Internet of Things Journal. 2018; 5:1; 269-282: ISSN: 2327-4662
Benslimane Y, BenAhmed K. Efficient End-to-End Secure Key Management Protocol for Internet of Things. International Journal of Electrical and Computer Engineering (IJECE). 2017; 7:6; 3622 3631 ISSN: 2088-8708.
Mahmood Z, Ning H, Ghafoor A. A Polynomial Subset-Based Efficient Multiparty Key Management System for Lightweight Device Networks. Sensors. 2017; 17(4): 670. doi:10.3390/s17040670
Mohammad M. Internet of Things: A Comprehensive Overview on Protocols, Architectures, Technologies, Simulation Tools, and Future Directions. Energies. 2023; 16.8:3465.
Gerodimos A, Maglaras L, Ferrag MA, Ayres N, Kantzavelou I. IoT: Communication protocols and security threats. Internet Things Cyber-Phys. Syst.2023; 3: 1–13.
Domínguez-Bolaño T, Campos O, Barral V, Escudero CJ, García-Naya JA. An overview of IoT architectures, technologies, and existing open-source projects. Internet Things. 2022; 20:
Python Own Certificate Authority (ownca). https://packagegalaxy.com/python/ownca.
Leshem G, Domb M. Strengthening IoT Network Protocols: A Model Resilient Against Cyber Attacks. IgMin Res. Feb 12, 2024; 2(2): 084-096. IgMin ID: igmin149; DOI: 10.61927/igmin149; Available at: www.igminresearch.com/articles/pdf/igmin149.pdf
次のリンクを共有した人は、このコンテンツを読むことができます:
Address Correspondence:
Guy Leshem, Department of Computer Science, Ashkelon Academic College (AAC), Ashkelon, Israel, Email: [email protected]; Menachem Domb, Department of Computer Science, Ashkelon Academic College (AAC), Ashkelon, Israel, Email: [email protected]
How to cite this article:
Leshem G, Domb M. Strengthening IoT Network Protocols: A Model Resilient Against Cyber Attacks. IgMin Res. Feb 12, 2024; 2(2): 084-096. IgMin ID: igmin149; DOI: 10.61927/igmin149; Available at: www.igminresearch.com/articles/pdf/igmin149.pdf
Copyright: © 2024 Leshem G, et al This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
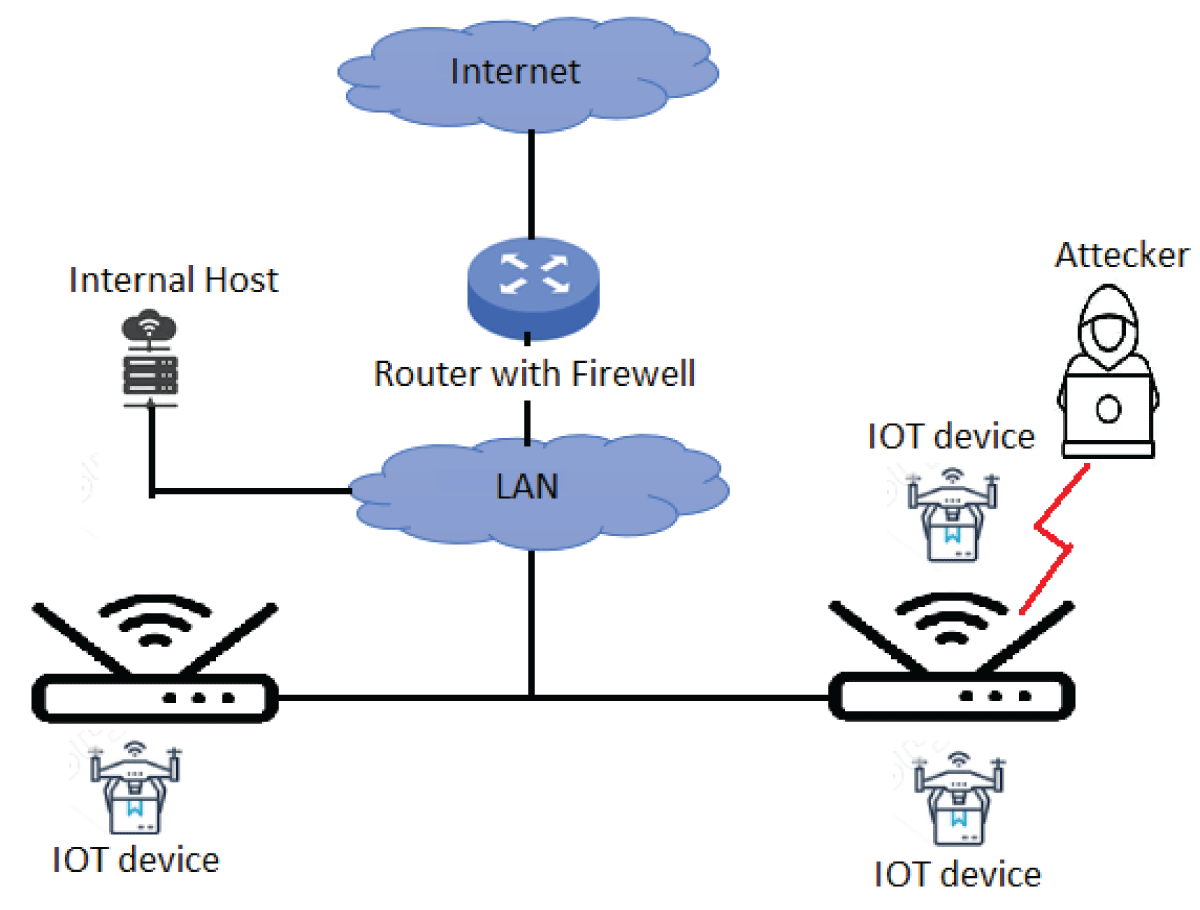 Figure 1: Demonstration of the parking lot attack....
Figure 1: Demonstration of the parking lot attack....
 Figure 2: Smart home concept based on IoT....
Figure 2: Smart home concept based on IoT....
 Figure 3: An example of the generated certificate for device...
Figure 3: An example of the generated certificate for device...
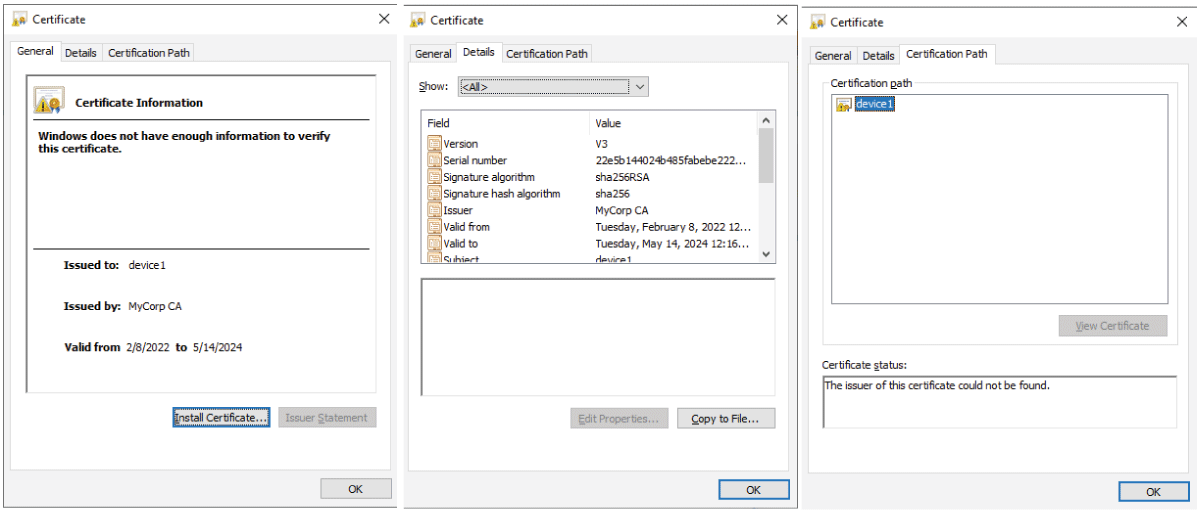 Figure 4: The Certificate of device#1 (for a sharp image, zo...
Figure 4: The Certificate of device#1 (for a sharp image, zo...
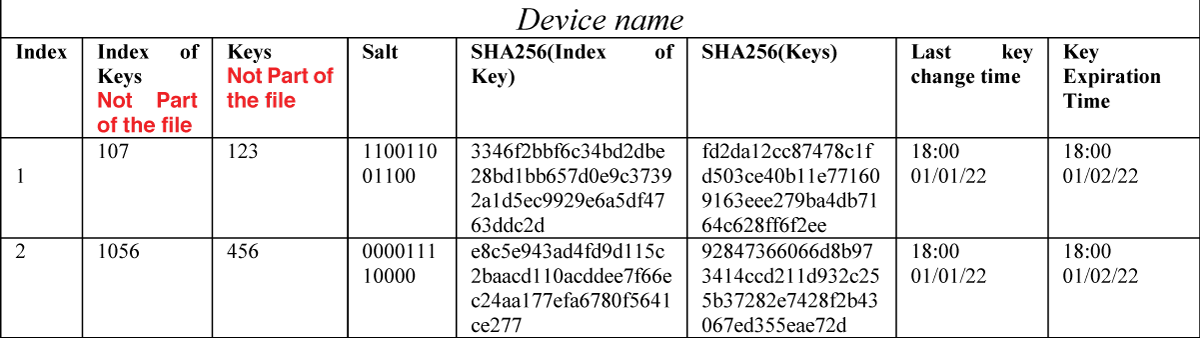 Figure 5: The structure of the keyword file....
Figure 5: The structure of the keyword file....
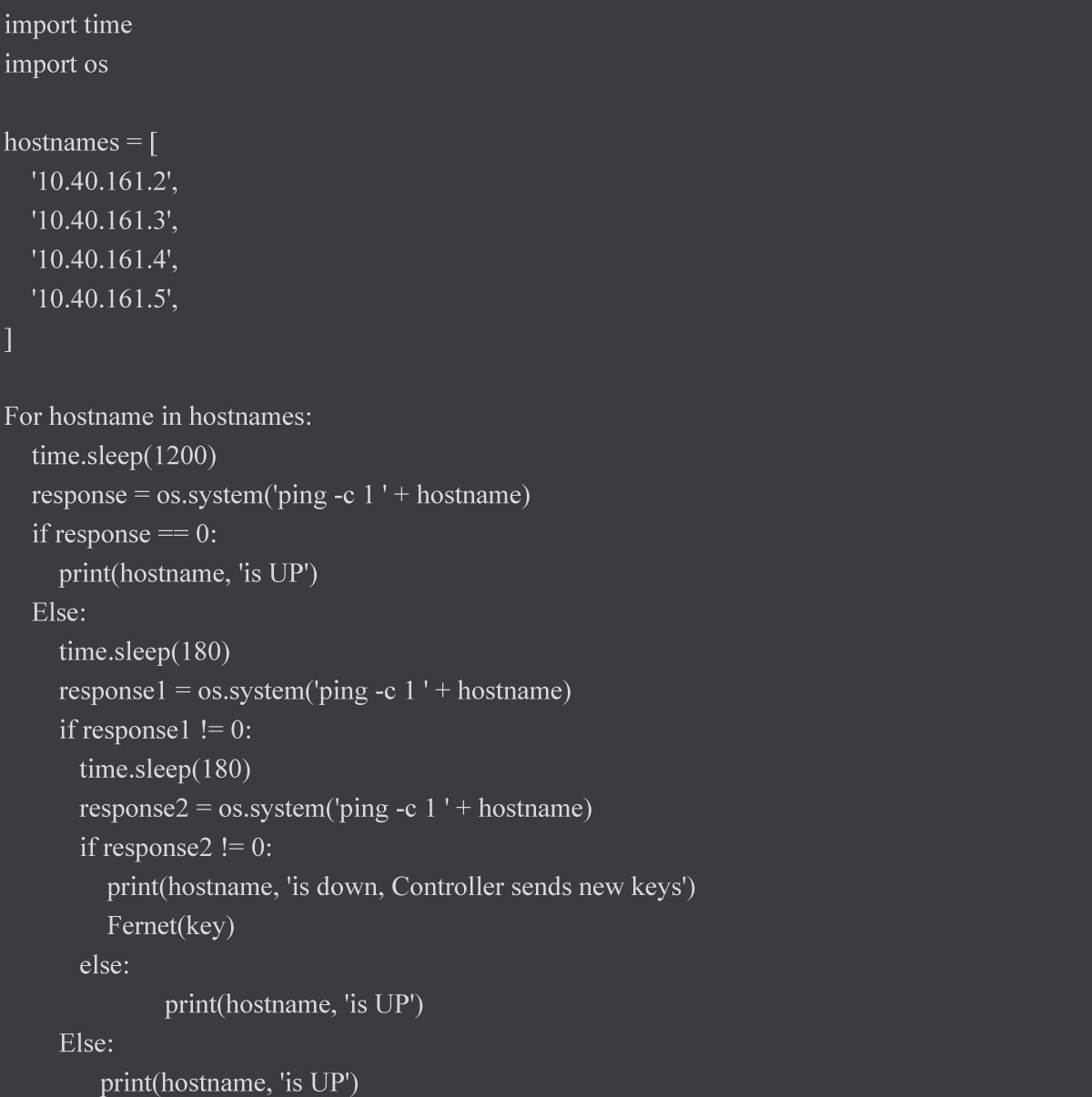 Figure 6: Python code for detecting missing devices....
Figure 6: Python code for detecting missing devices....
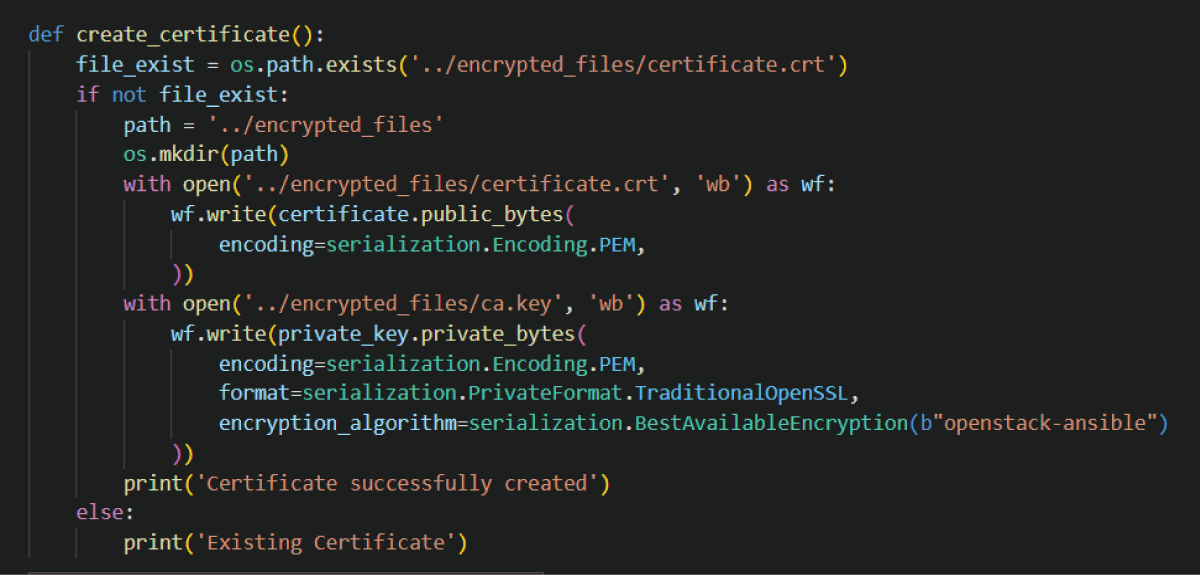 Figure 7: Python code for updating a local certificate for e...
Figure 7: Python code for updating a local certificate for e...
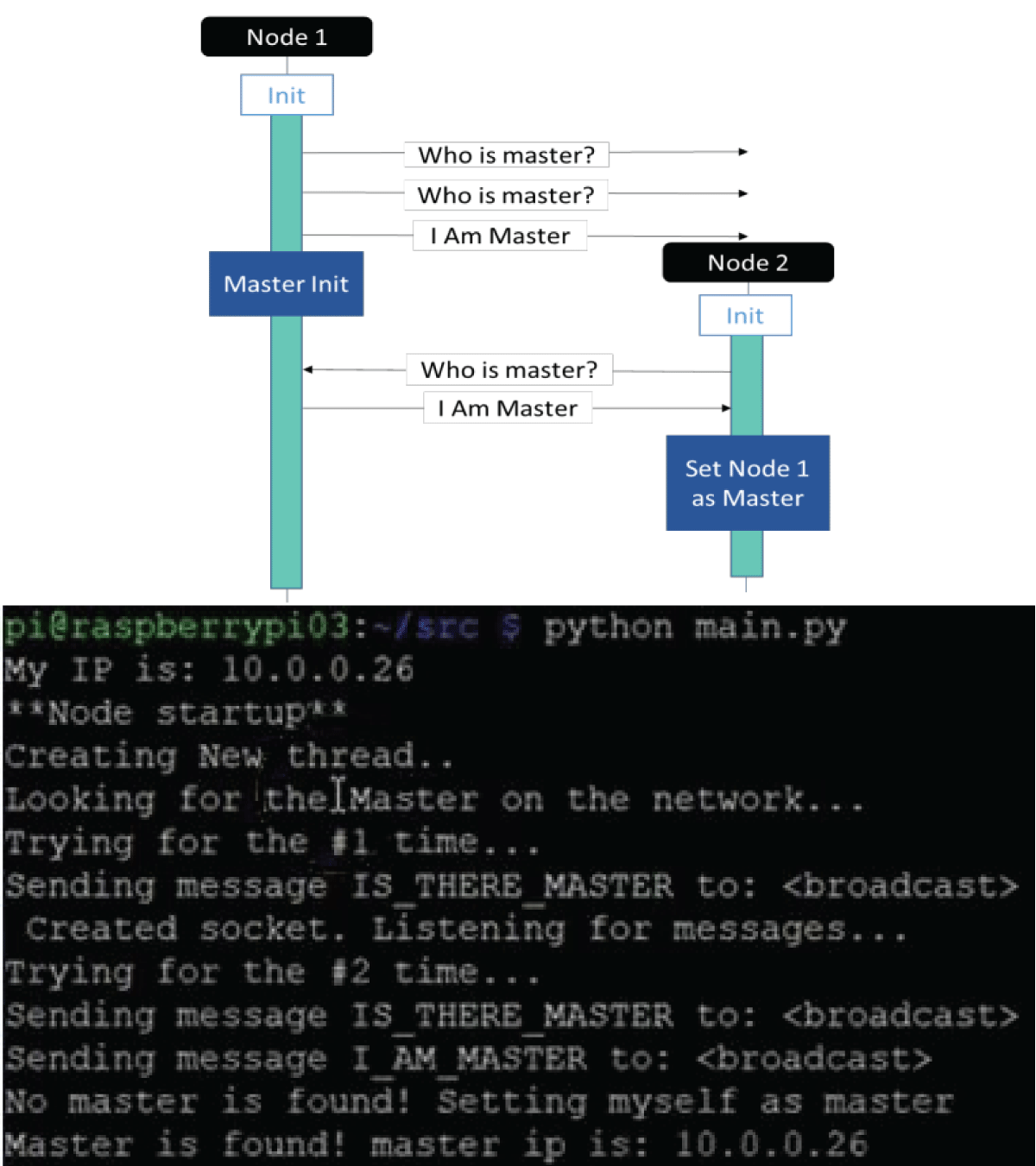 Figure 8: Python code results for determining who is the Con...
Figure 8: Python code results for determining who is the Con...
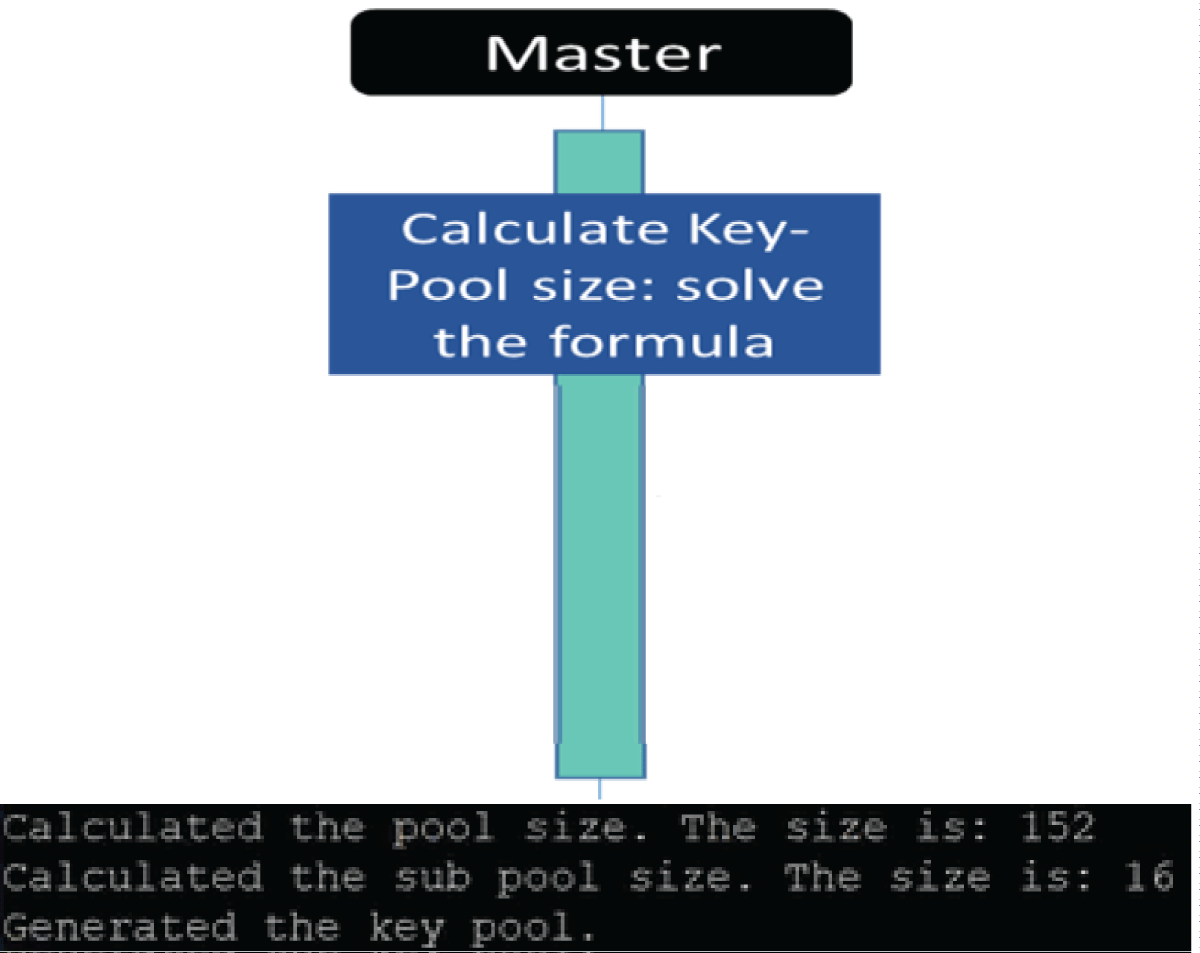 Figure 9: Python code results for defining the key-pool size...
Figure 9: Python code results for defining the key-pool size...
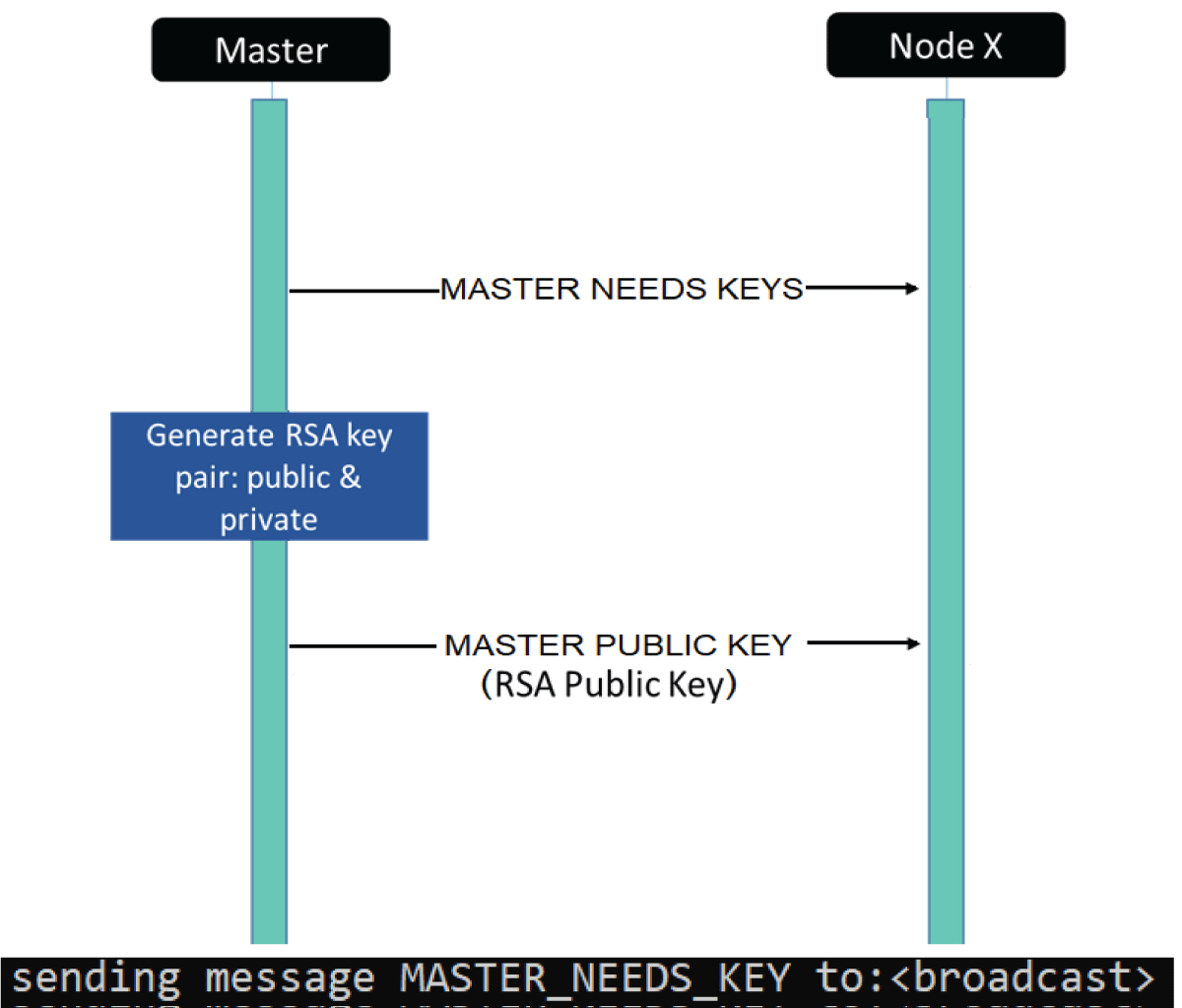 Figure 10: Python code results for distributing keys by the C...
Figure 10: Python code results for distributing keys by the C...
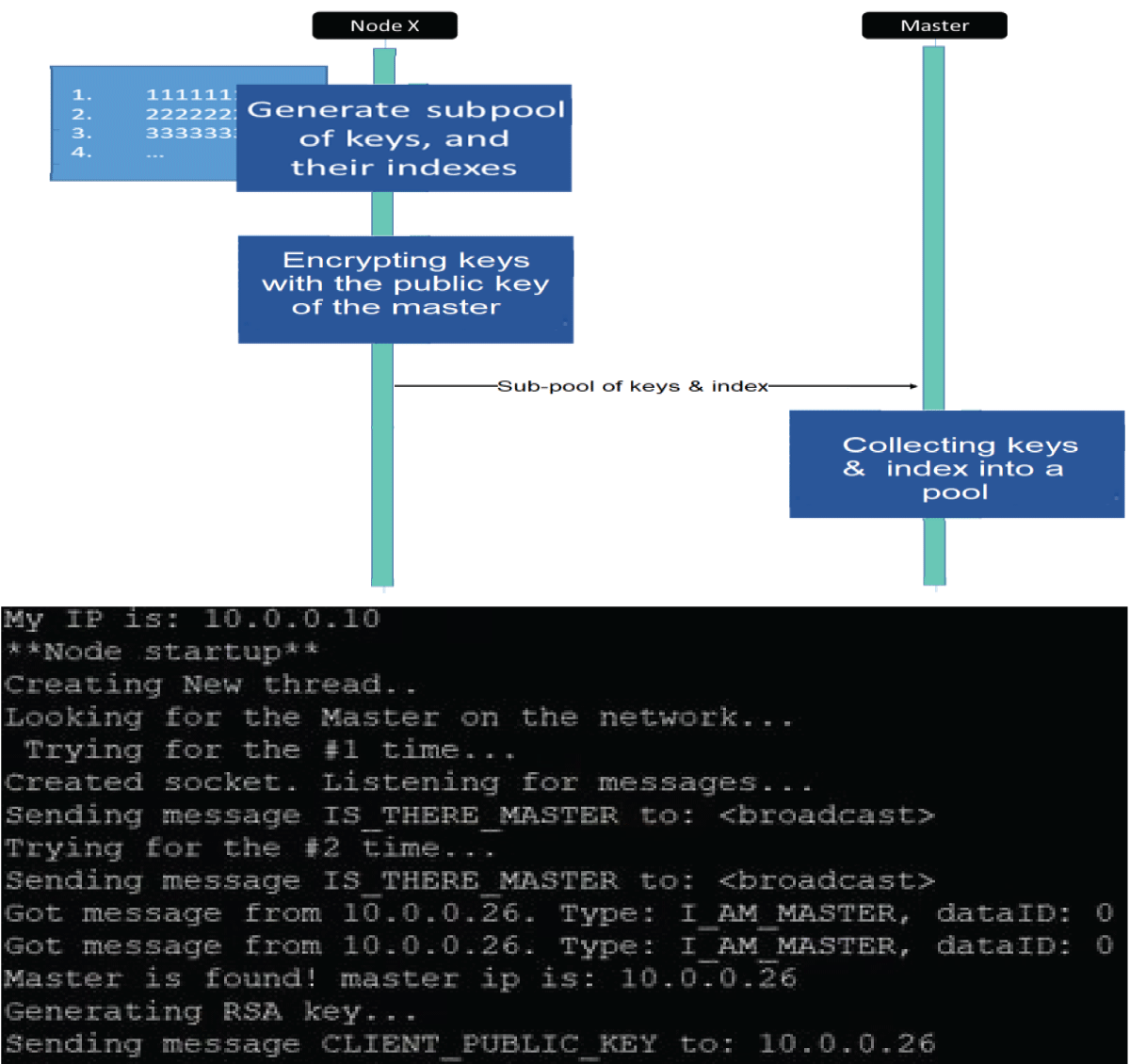 Figure 11: Python code results for the creation of distribute...
Figure 11: Python code results for the creation of distribute...
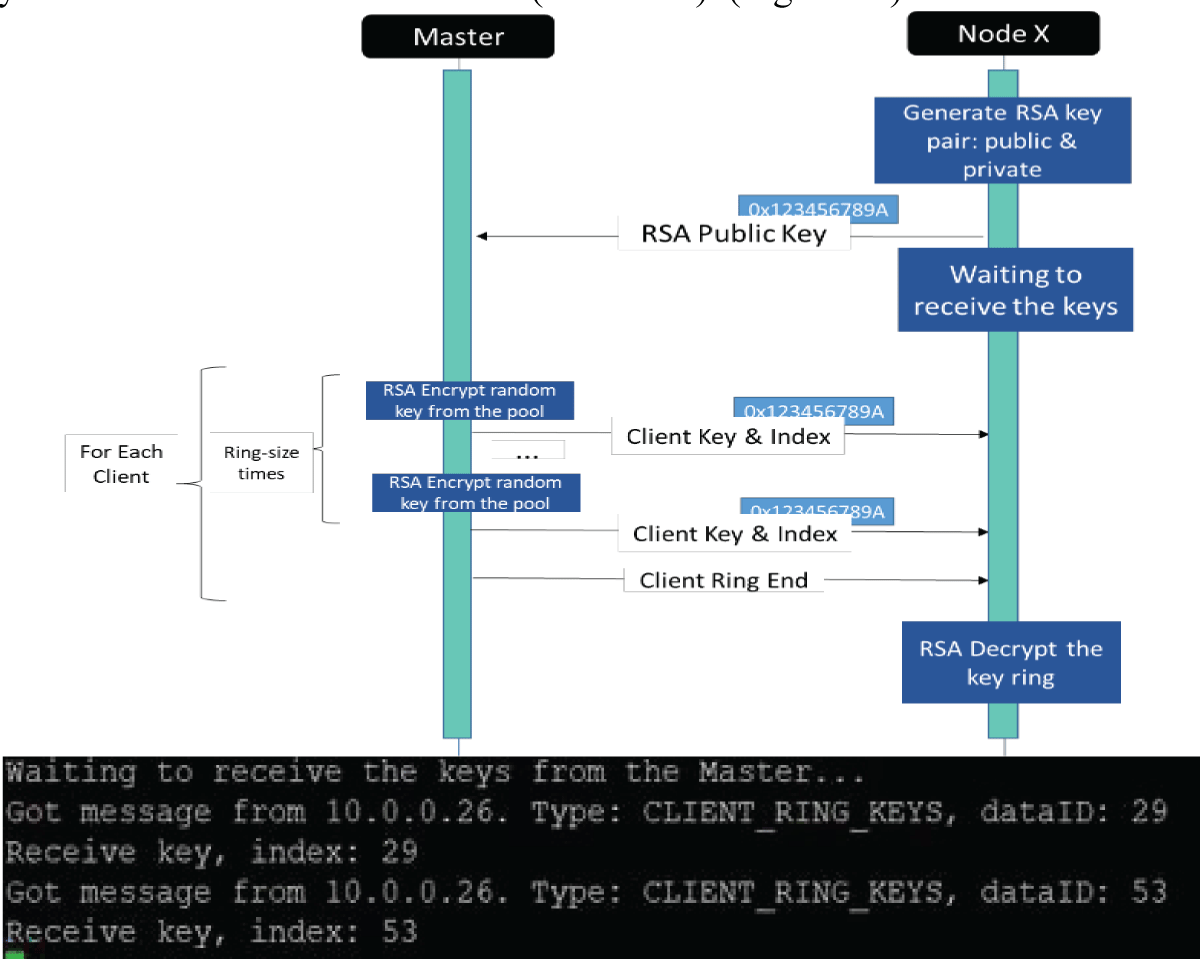 Figure 12: Python code results for generating a private and p...
Figure 12: Python code results for generating a private and p...
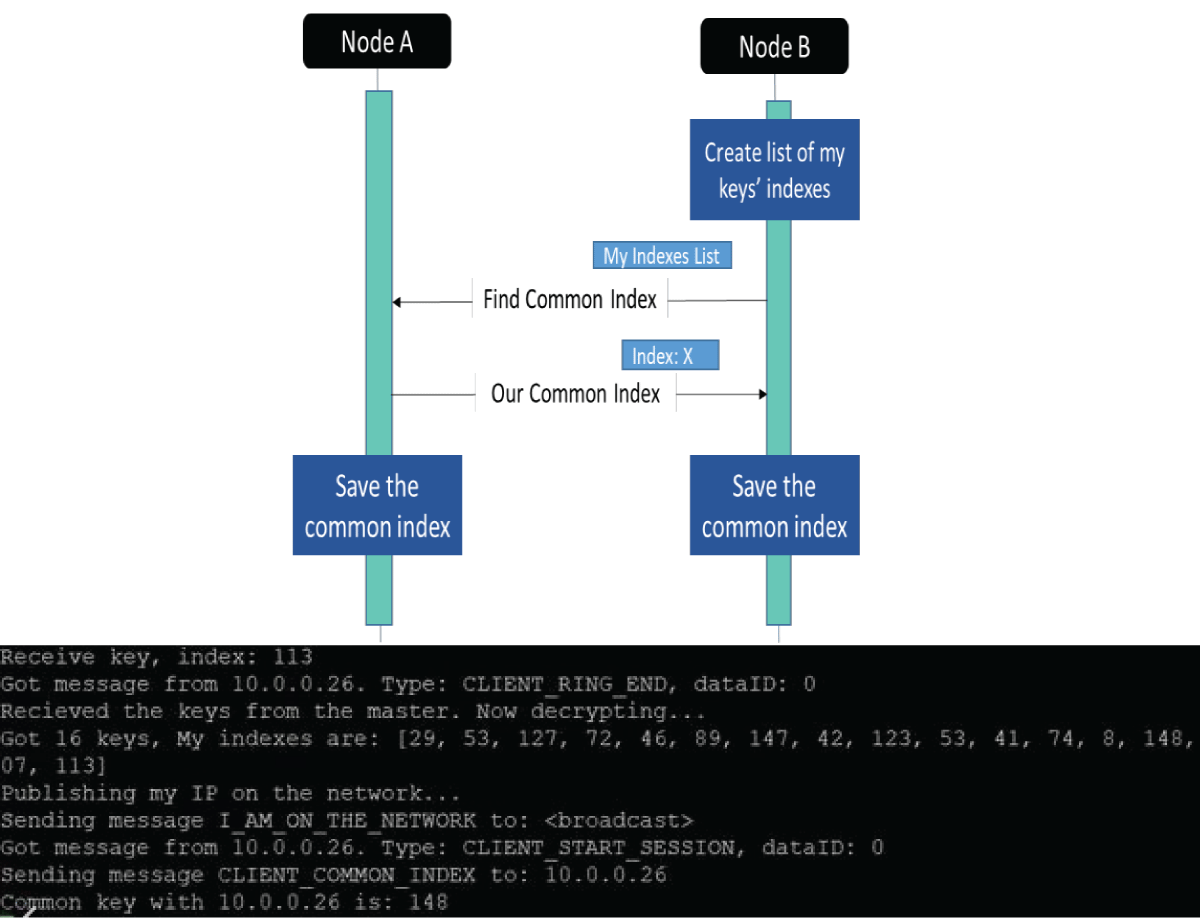 Figure 13: Python code results for finding a shared key....
Figure 13: Python code results for finding a shared key....
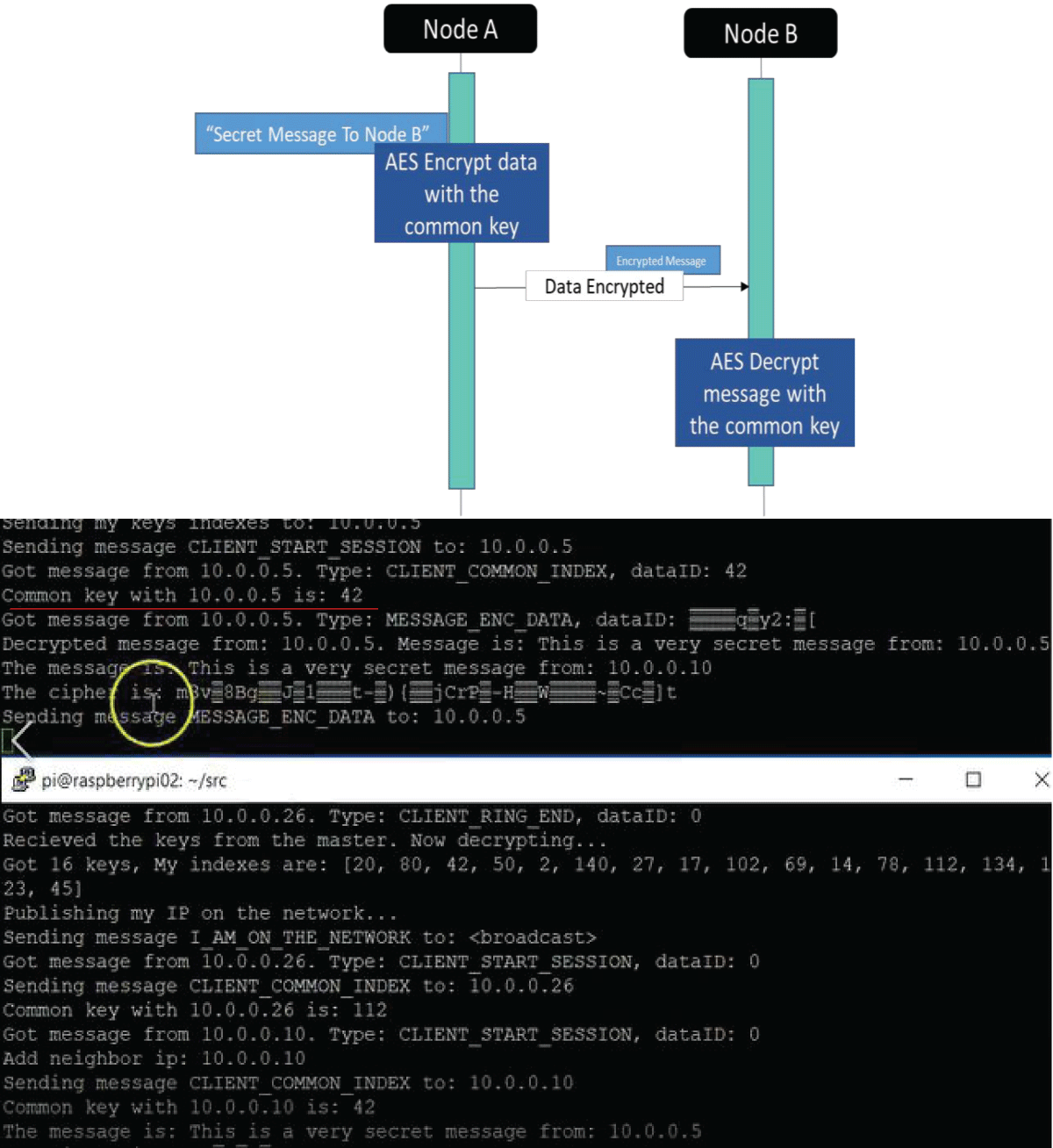 Figure 14: Python code results for communication between node...
Figure 14: Python code results for communication between node...
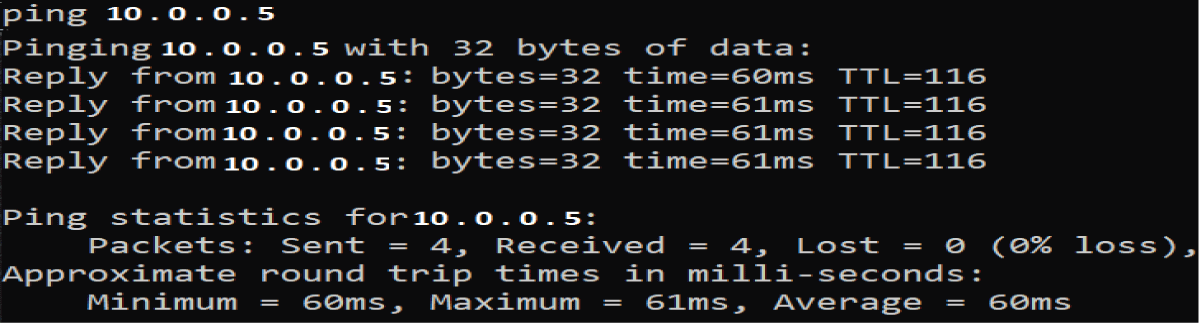 Figure 15: Python code results for detection of missing devic...
Figure 15: Python code results for detection of missing devic...
Leshem G, David E, Domb M. Probability-Based Keys Sharing for IoT Security. ICSEE International Conference on the Science of Electrical Engineering. 2018.
Gubbi J, Buyya R, Marusic S, Palaniswami M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013; 29:1645–1660.
Sundmaeker H, Guillemin P, Friess P, Woelfflé S. Vision and challenges for realizing the Internet of Things. In Cluster of European Research Projects on the Internet of Things; European Commission: Brussels, 2010; 3: 34–36.
Stellios I, Kotzanikolaou P, Psarakis M, Alcaraz C, Lopez J. A survey of IoT-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Commun. Surv. Tutor. 2018; 20:3453–3495.
Eschenauer L, Gligor VD. A key-management scheme for distributed sensor networks. Proceedings of the 9th ACM conference on Computer and communications security, Washington DC.11-2002; 341-47.
Alagheband MR, Aref MR. Dynamic and secure key management model for hierarchical heterogeneous sensor networks. Iet Information Security [IF: 1.04]. DOI — 10.1049/iet-ifs.2012.0144, 2012
Sciancalepore S, Piro G, Boggia G, Bianchi G. Key Management Protocol with Implicit Certificates for IoT systems. Proceedings of the 2015 Workshop on IoT challenges in Mobile and Industrial Systems. Florence, Italy. ACM, NY, USA. 2015; 37-42. ISBN: 978-1-4503-3502-7
Roman R, Alcaraz C, Lopez J. Key management systems for sensor networks in the context of the Internet of Things. Nicolas Sklavos, Computers & Electrical Engineering. 2011; 37:2; Pages 147-159.
Wazid M, Das AK, Odelu V. Design of Secure User Authenticated Key Management Protocol for Generic IoT Networks. IEEE Internet of Things Journal. 2018; 5:1; 269-282: ISSN: 2327-4662
Benslimane Y, BenAhmed K. Efficient End-to-End Secure Key Management Protocol for Internet of Things. International Journal of Electrical and Computer Engineering (IJECE). 2017; 7:6; 3622 3631 ISSN: 2088-8708.
Mahmood Z, Ning H, Ghafoor A. A Polynomial Subset-Based Efficient Multiparty Key Management System for Lightweight Device Networks. Sensors. 2017; 17(4): 670. doi:10.3390/s17040670
Mohammad M. Internet of Things: A Comprehensive Overview on Protocols, Architectures, Technologies, Simulation Tools, and Future Directions. Energies. 2023; 16.8:3465.
Gerodimos A, Maglaras L, Ferrag MA, Ayres N, Kantzavelou I. IoT: Communication protocols and security threats. Internet Things Cyber-Phys. Syst.2023; 3: 1–13.
Domínguez-Bolaño T, Campos O, Barral V, Escudero CJ, García-Naya JA. An overview of IoT architectures, technologies, and existing open-source projects. Internet Things. 2022; 20:
Python Own Certificate Authority (ownca). https://packagegalaxy.com/python/ownca.