要約
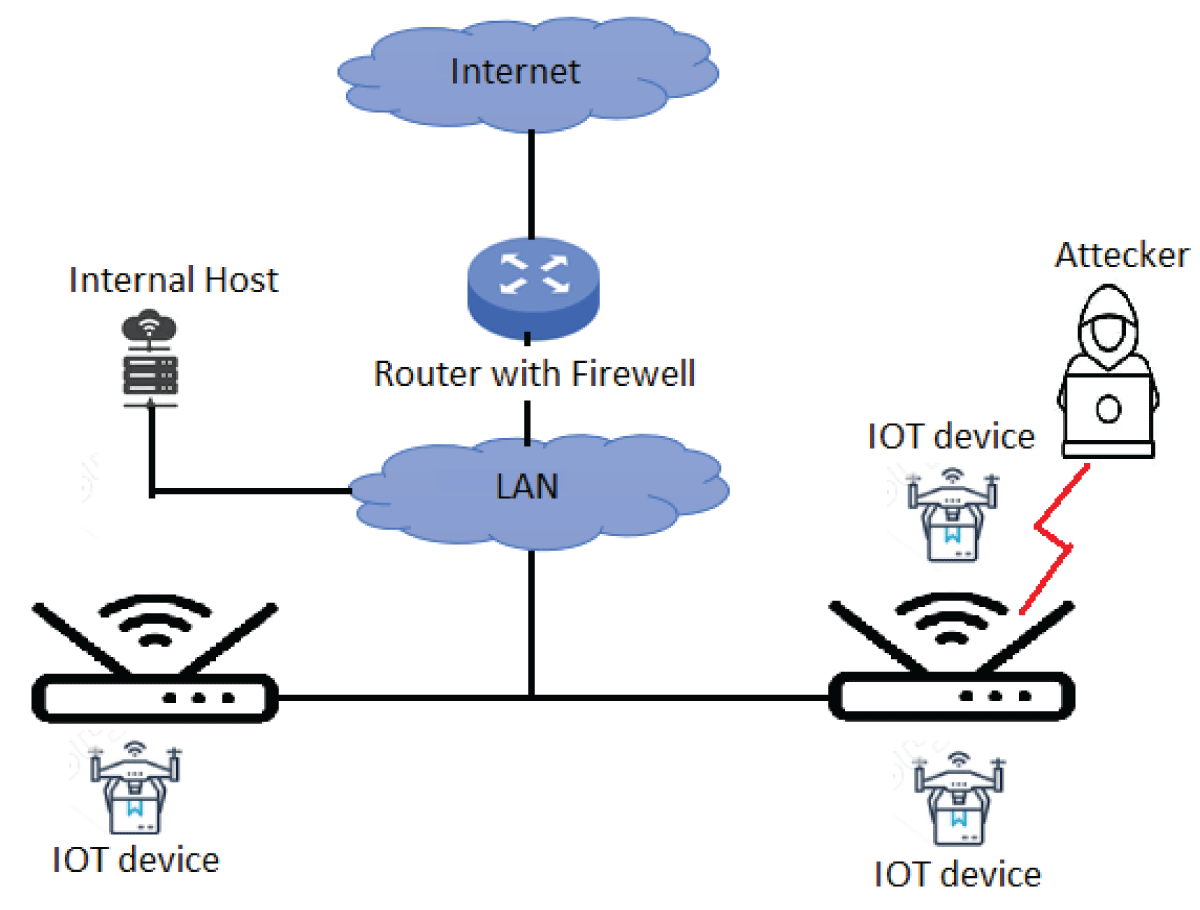
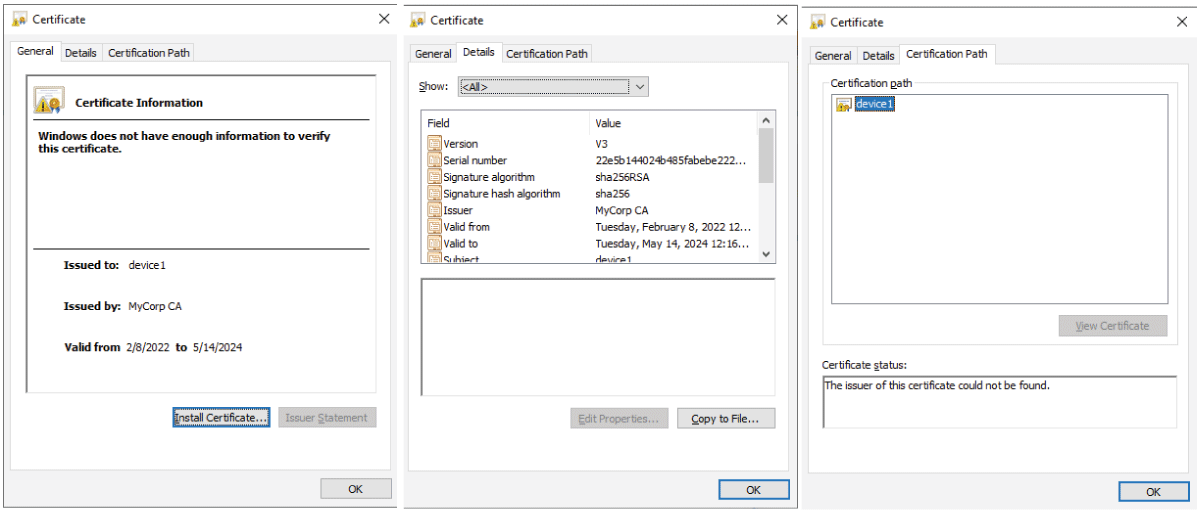
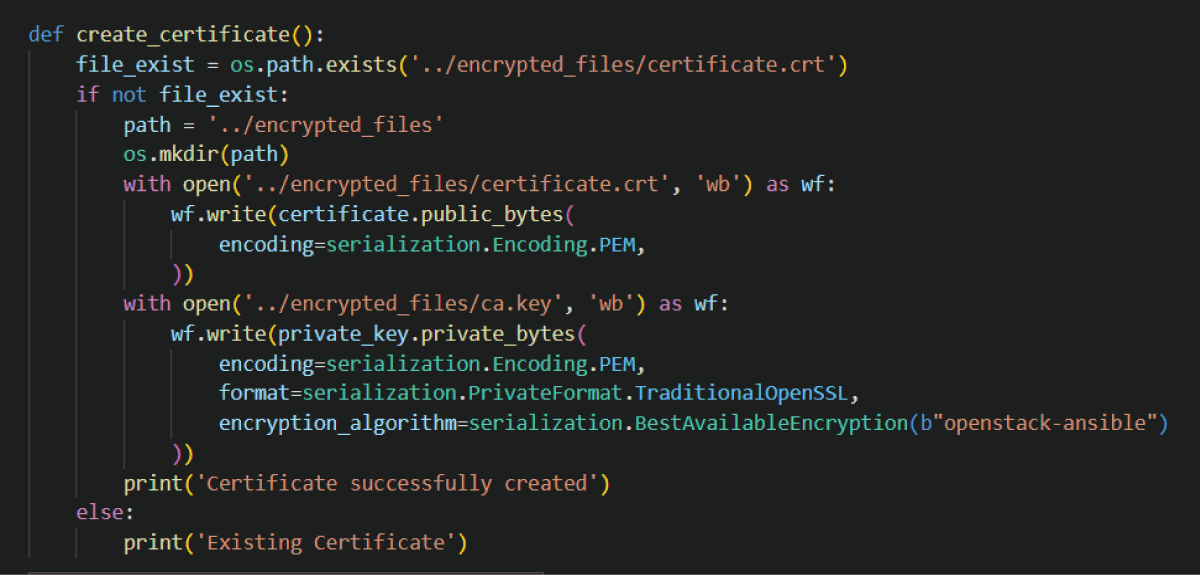
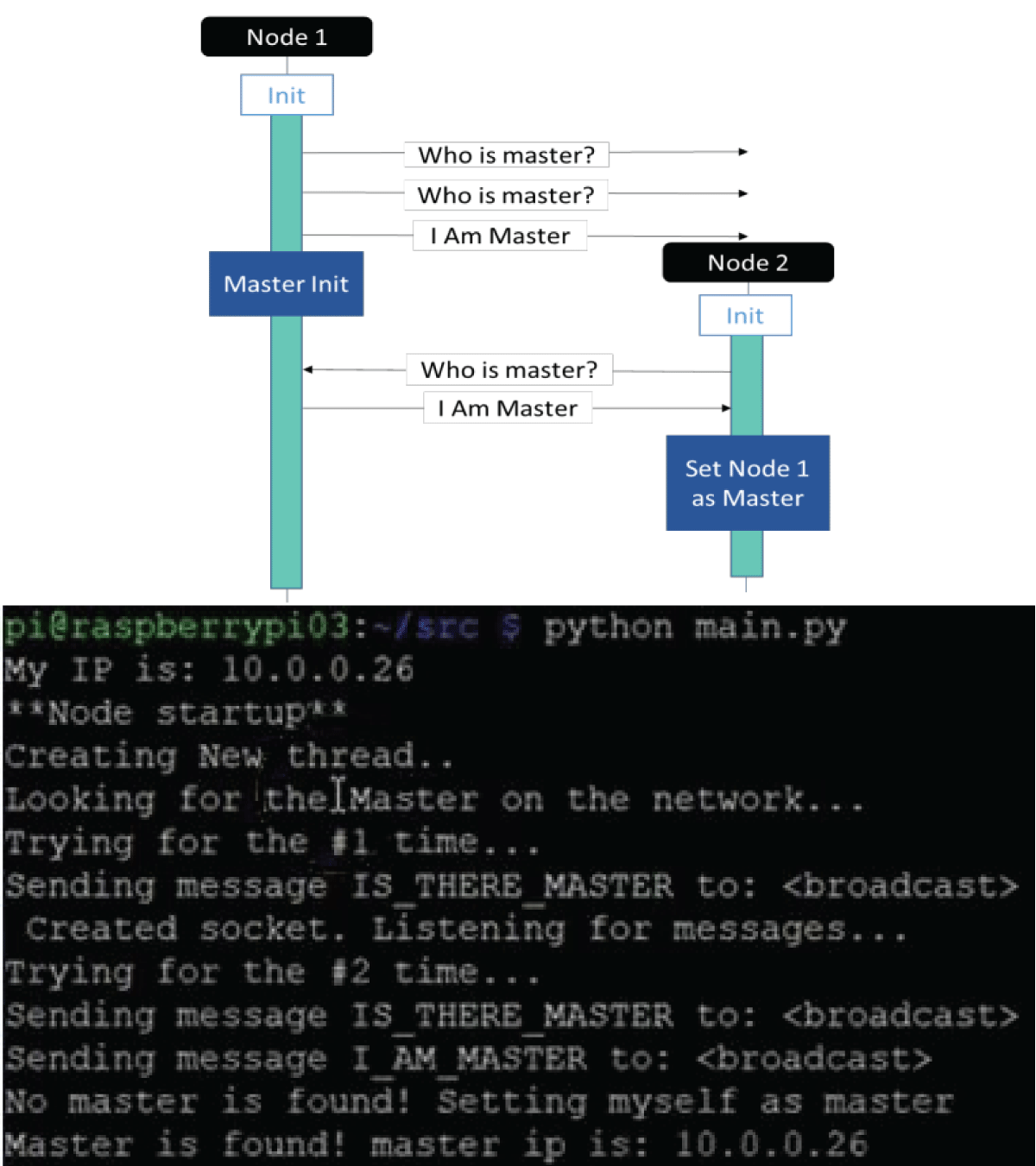
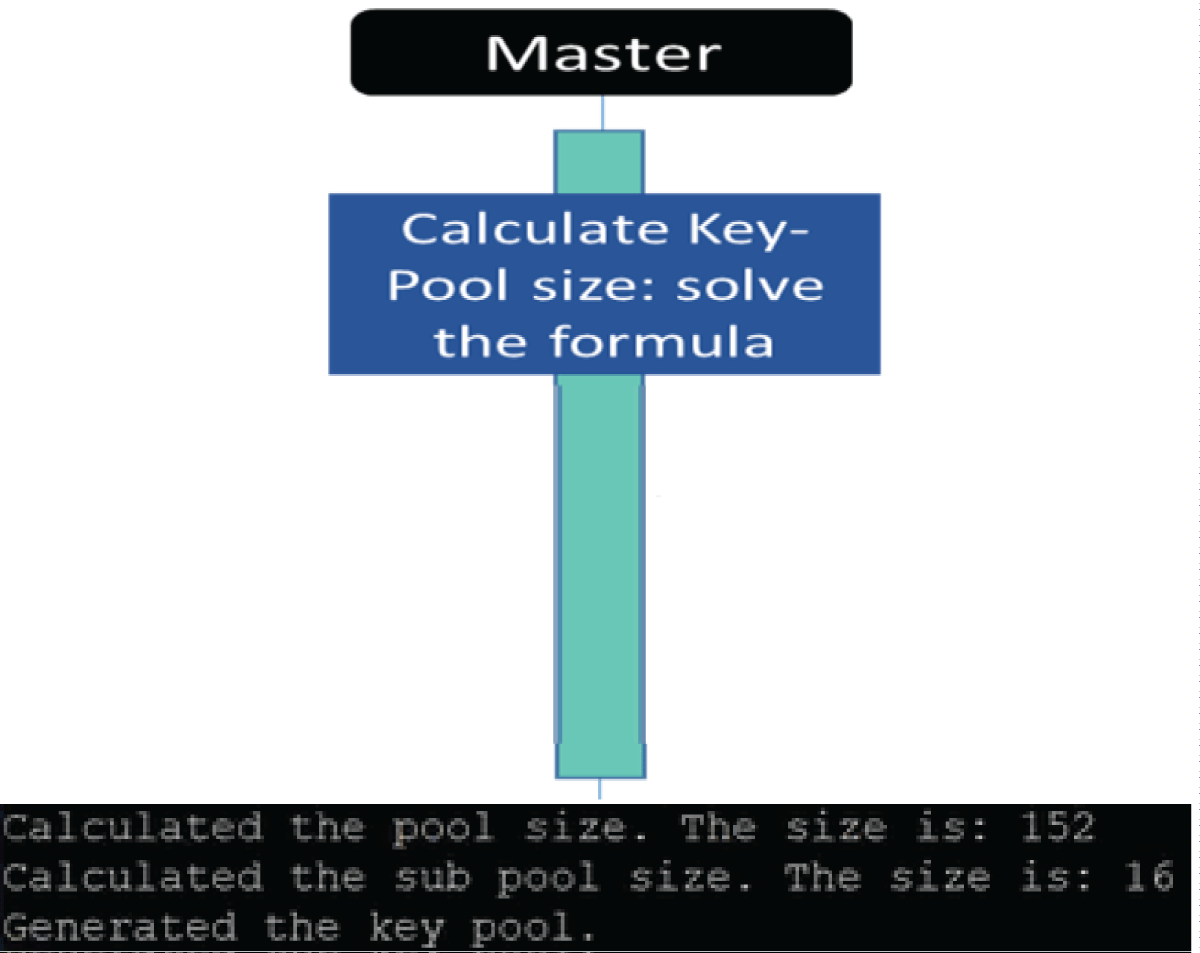
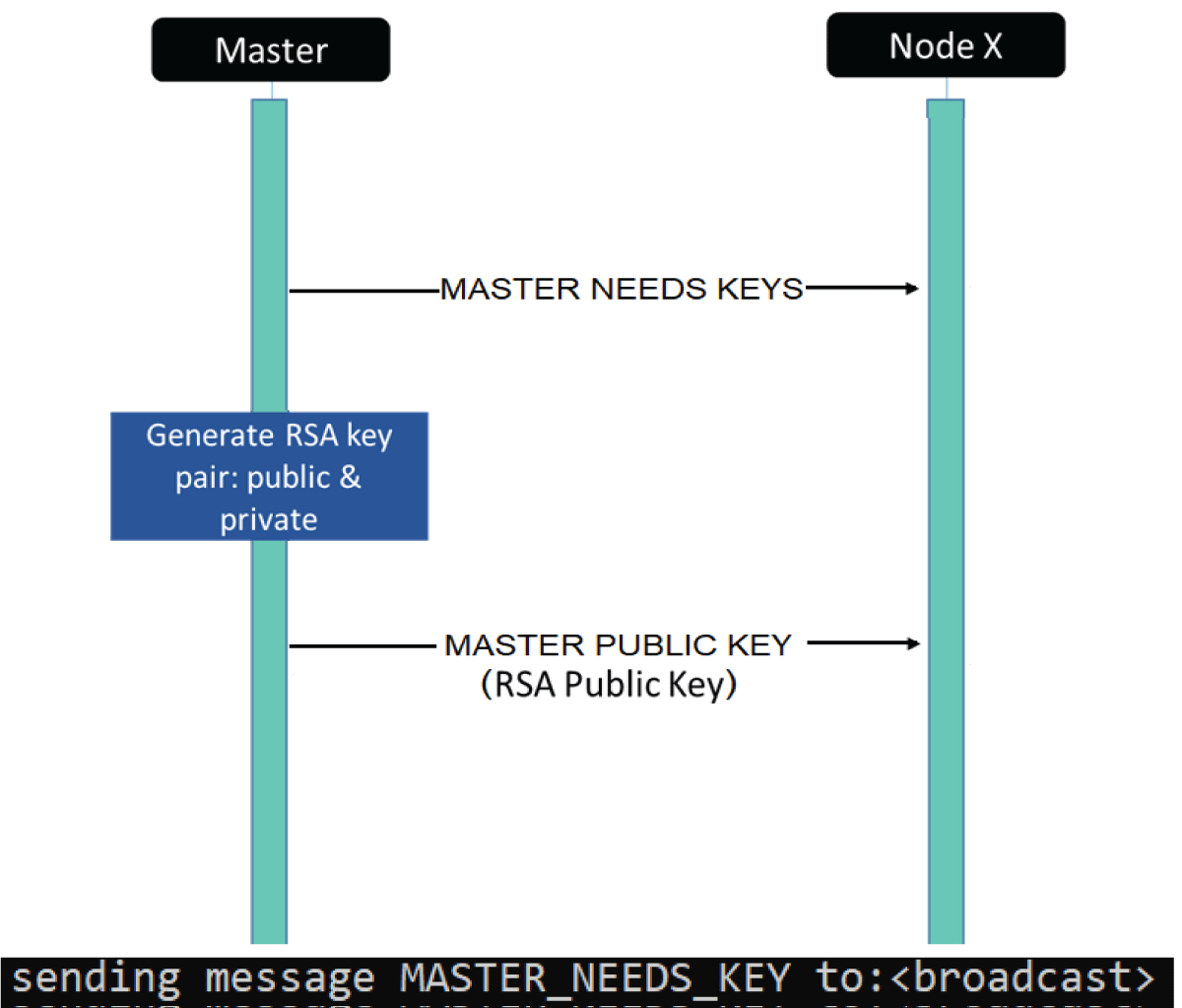
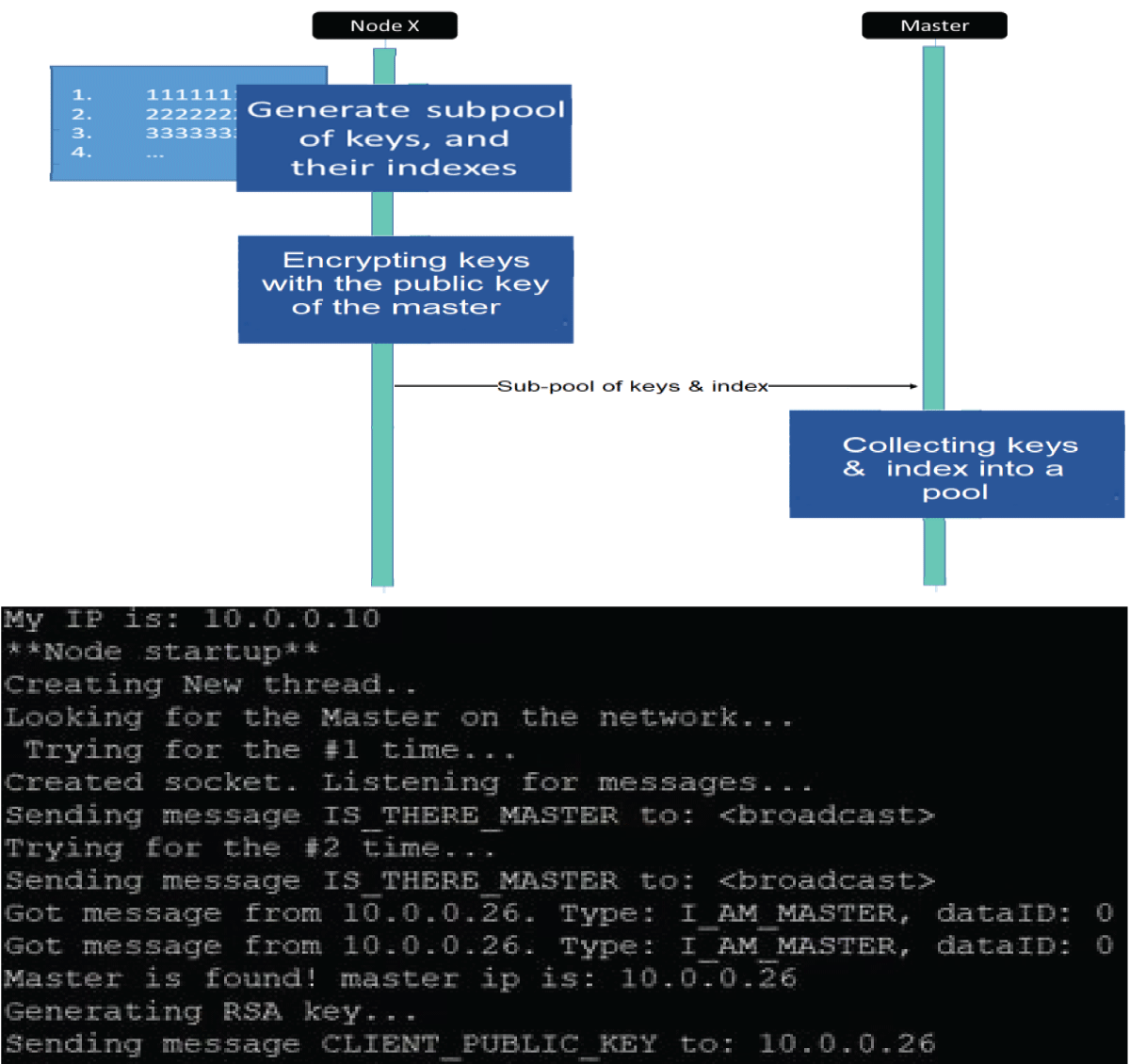
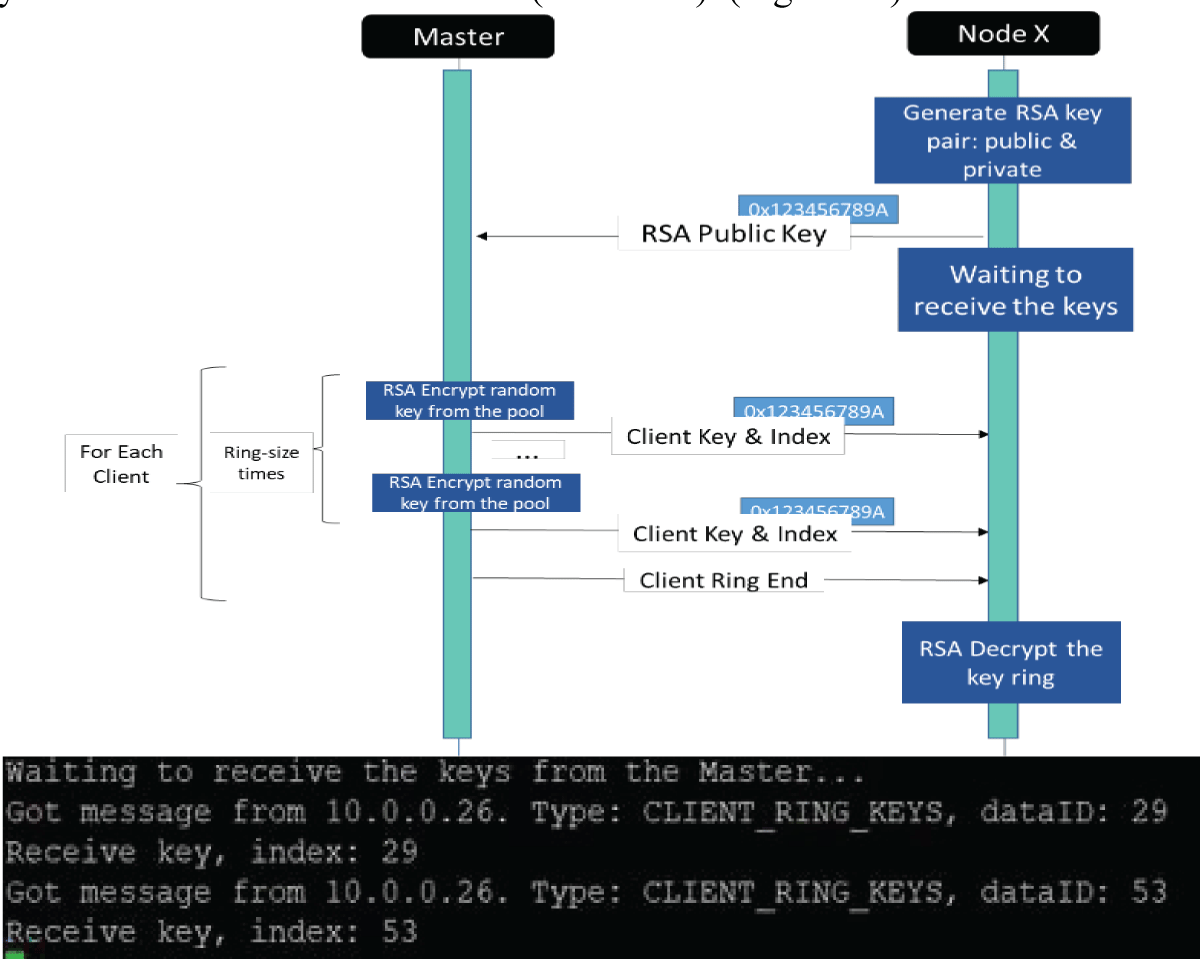
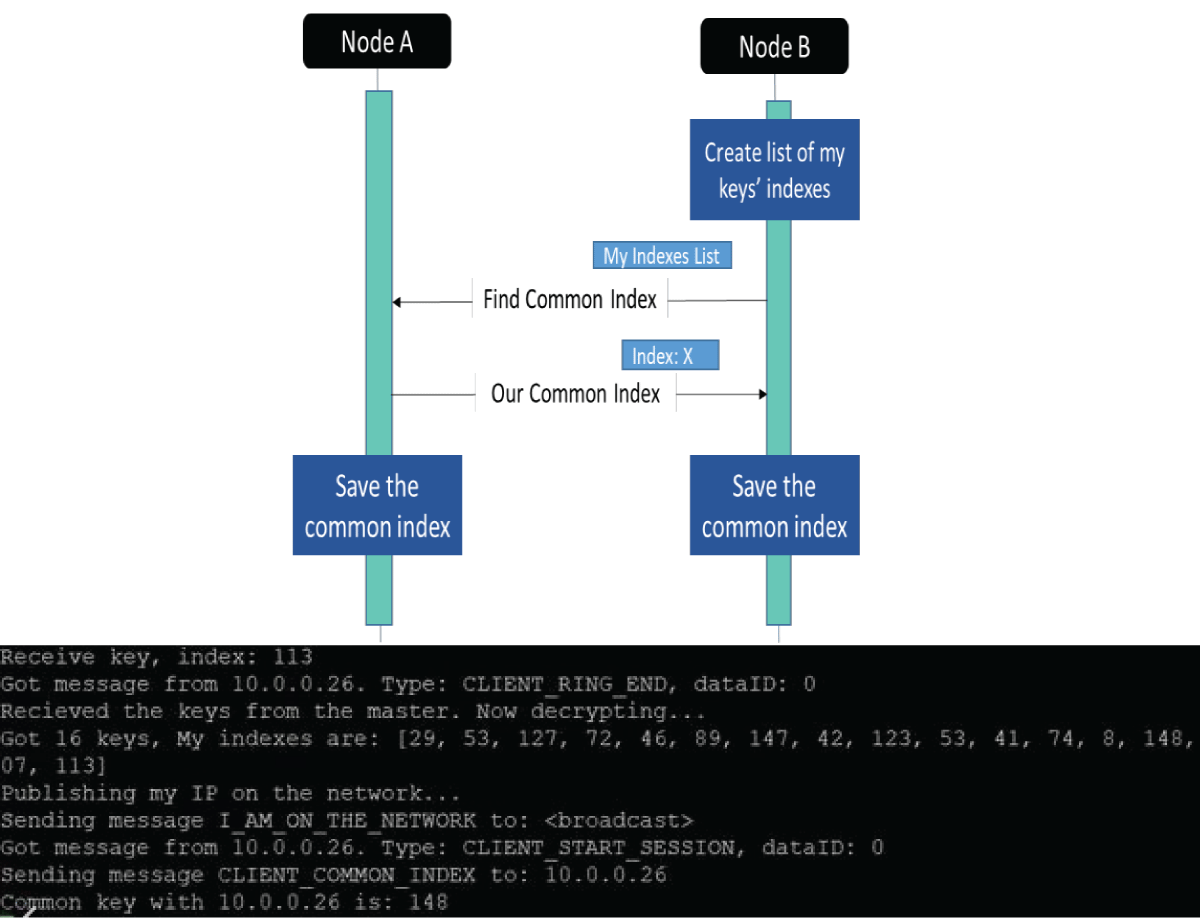
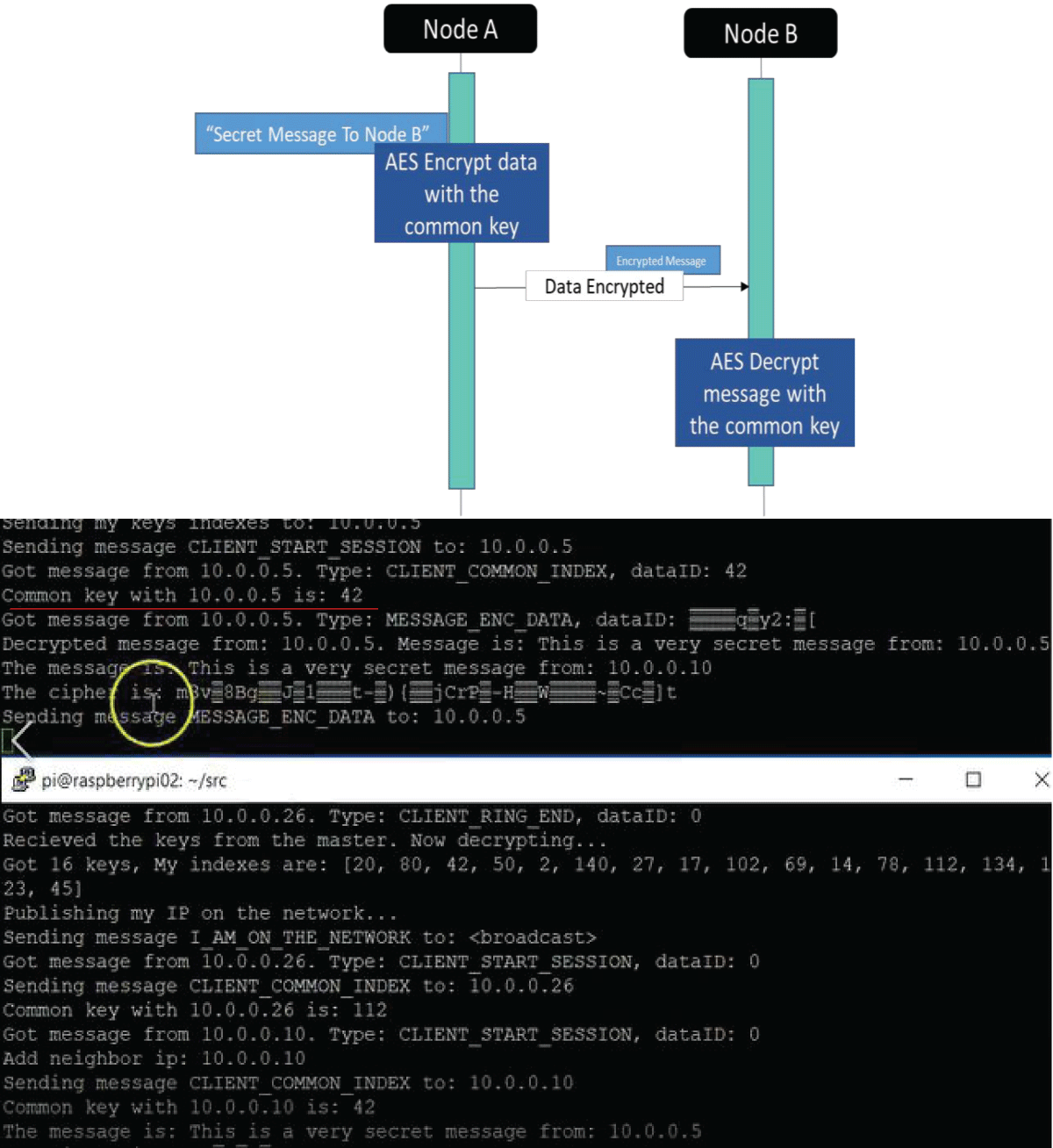
The pervasive Internet of Things (IoT) integration has revolutionized industries such as medicine, environmental care, and urban development. The synergy between IoT devices and 5G cellular networks has further accelerated this transformation, providing ultra-high data rates and ultra-low latency. This connectivity enables various applications, including remote surgery, autonomous driving, virtual reality gaming, and AI-driven smart manufacturing. However, IoT devices’ real-time and high-volume messaging nature exposes them to potential malicious attacks. The implementation of encryption in such networks is challenging due to the constraints of IoT devices, including limited memory, storage, and processing bandwidth. In a previous work [1], we proposed an ongoing key construction process, introducing a pivotal pool to enhance network security. The protocol is designed with a probability analysis to ensure the existence of a shared key between any pair of IoT devices, with the predefined probability set by the system designer. However, our earlier model faced vulnerabilities such as the “parking lot attack” and physical attacks on devices, as highlighted in the conclusion section. We present a complementary solution to address these issues, fortifying our previous protocol against cyber threats. Our approach involves the implementation of an internal Certification Authority (CA) that issues certificates for each IoT device before joining the network.
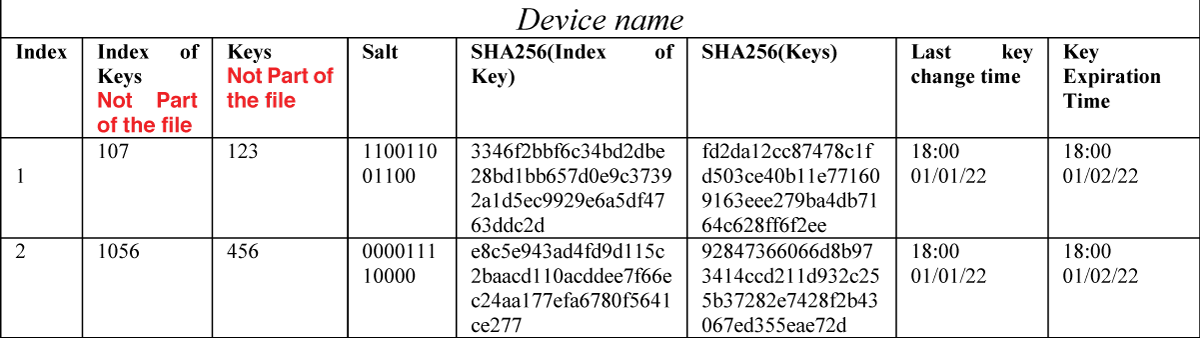
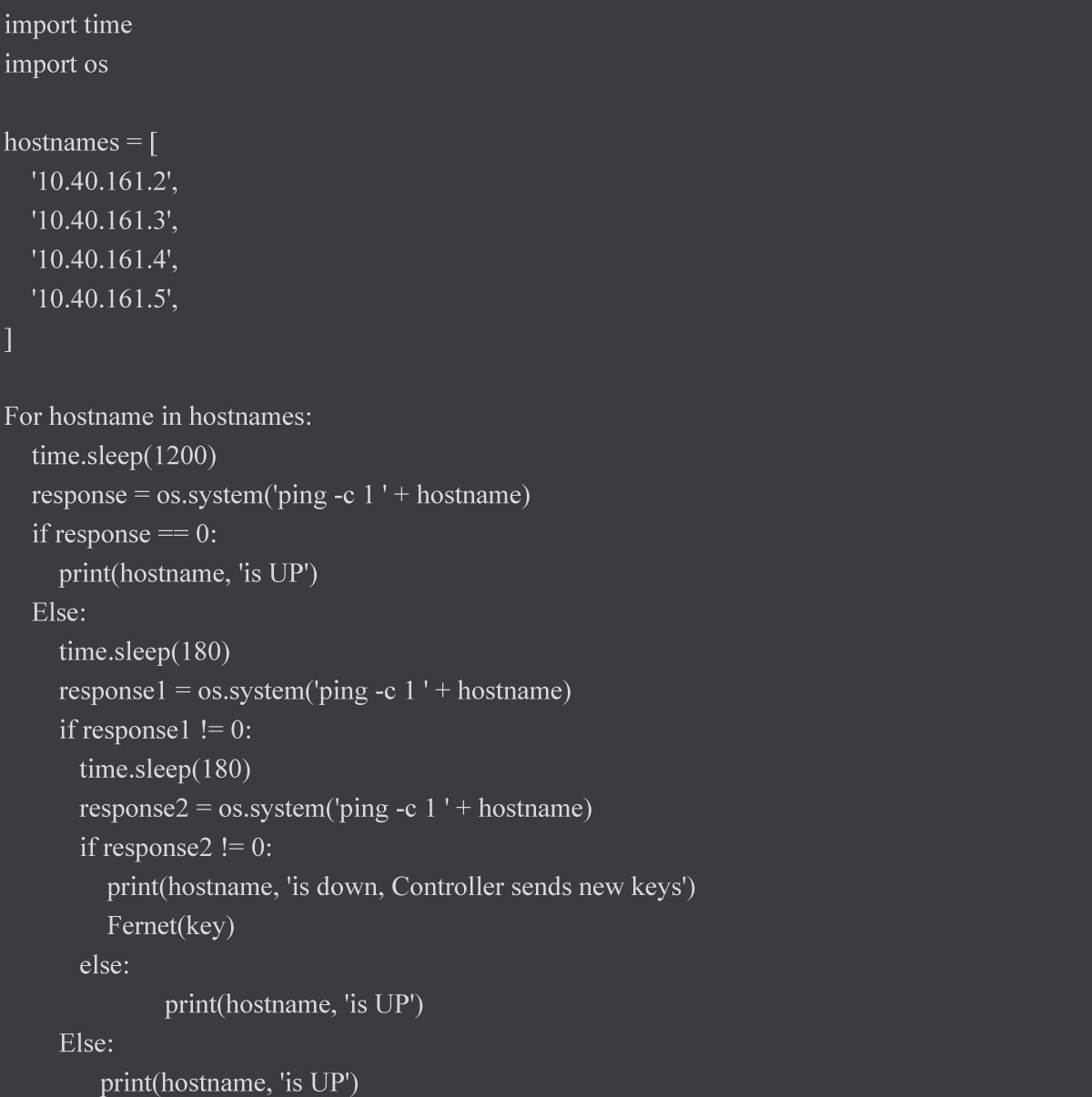
Furthermore, all encryption keys are distributed by the primary IoT device using the Unix OS ‘passwd’ mechanism. If a device “disappears,” all encryption keys are promptly replaced, ensuring continuous resilience against potential security breaches. This enhanced protocol establishes a robust security framework for IoT networks, safeguarding against internal and external threats.